Ensuring the backup of our data is essential to safeguard its accuracy and accessibility (the subject matter experts would call them integrity and availability, from the CIA triad, where the C stands for confidentiality). In other words, creating copies of our data is crucial to make sure it stays intact and can be retrieved in case of need.
ISO 22301 “Societal security -- Business continuity management systems --- Requirements” suggests some steps of a backup strategy:
1. Risk Assessment
2. Define Information Security Policy
3. Business Impact Analysis (BIA)
4. Develop a Backup Strategy
5. Access Controls and Encryption
6. Regular Testing and Exercising
7. Documentation and Records
8. Incident Response Planning
9. Monitoring and Continuous Improvement
10. Training and Awareness
11. Compliance with Legal and Regulatory Requirements
In the “Business Impact Analysis” step it is paramount to undersand a couple of easy metrics in order to correctly dimension and setup a backup strategy:
1. Recovery Point Objective (RPO)
2. Maximum Tolerable Downtime (MTD)
3. Recovery Time Objective (RTO)
4. Work Recovery Time (WRT)
The picture below should help in understanding their meaning:
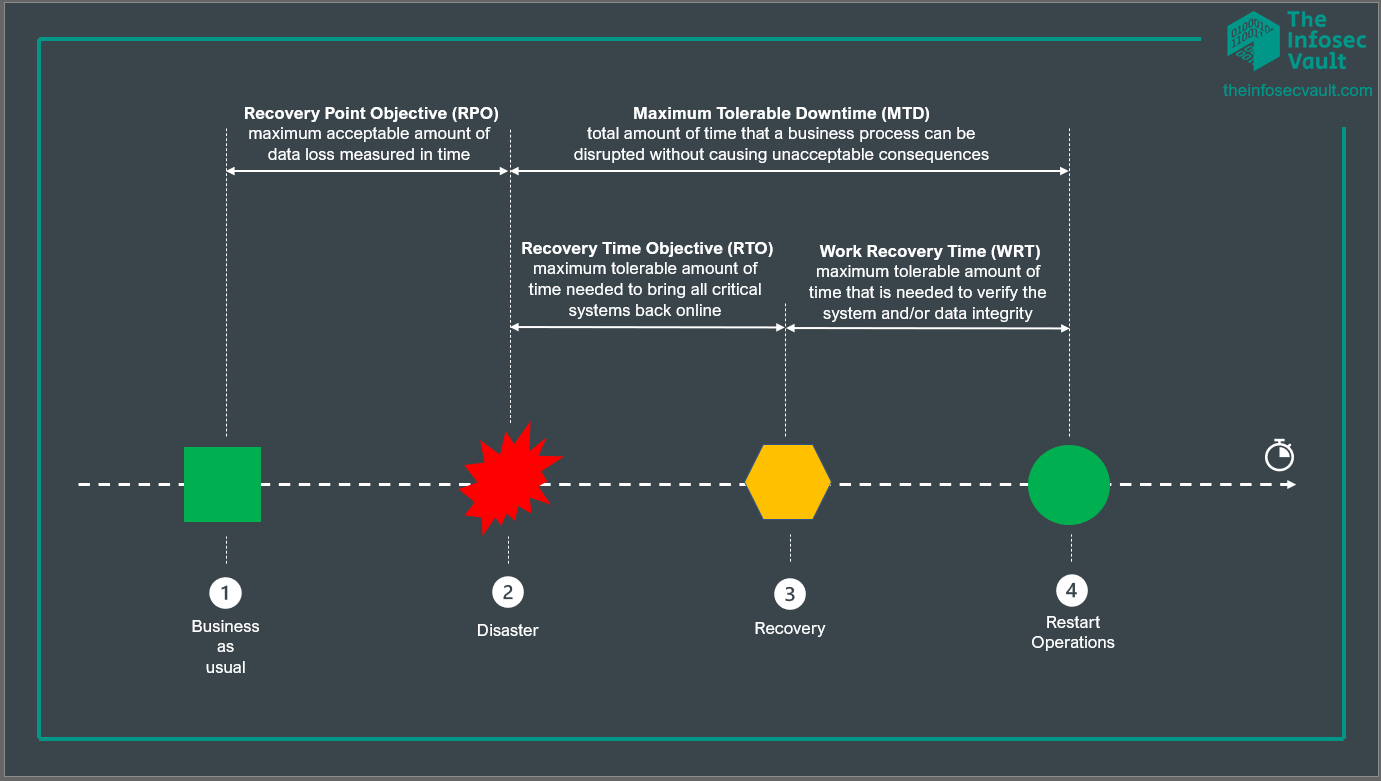
The worth of your data and the budget you have will determine how far you can reduce Recovery Point Objective (RPO) and Maximum Tolerable Downtime (MTD) to zero. You can cut down on the amount of time it takes to recover your systems and data by putting in place a continuous replication plan that mirrors data continuously in real-time.
Put another way, continuous replication guarantees that, in the case of a disruption, there will be nearly no data loss (zero RPO) and minimum downtime (zero MTD) if your data is really valuable and you have the financial means to support it.
If A zero RPO / sero MTD strategy is not affordable for you then 2 main things should be kept in mind (and well documented in your backup policies).
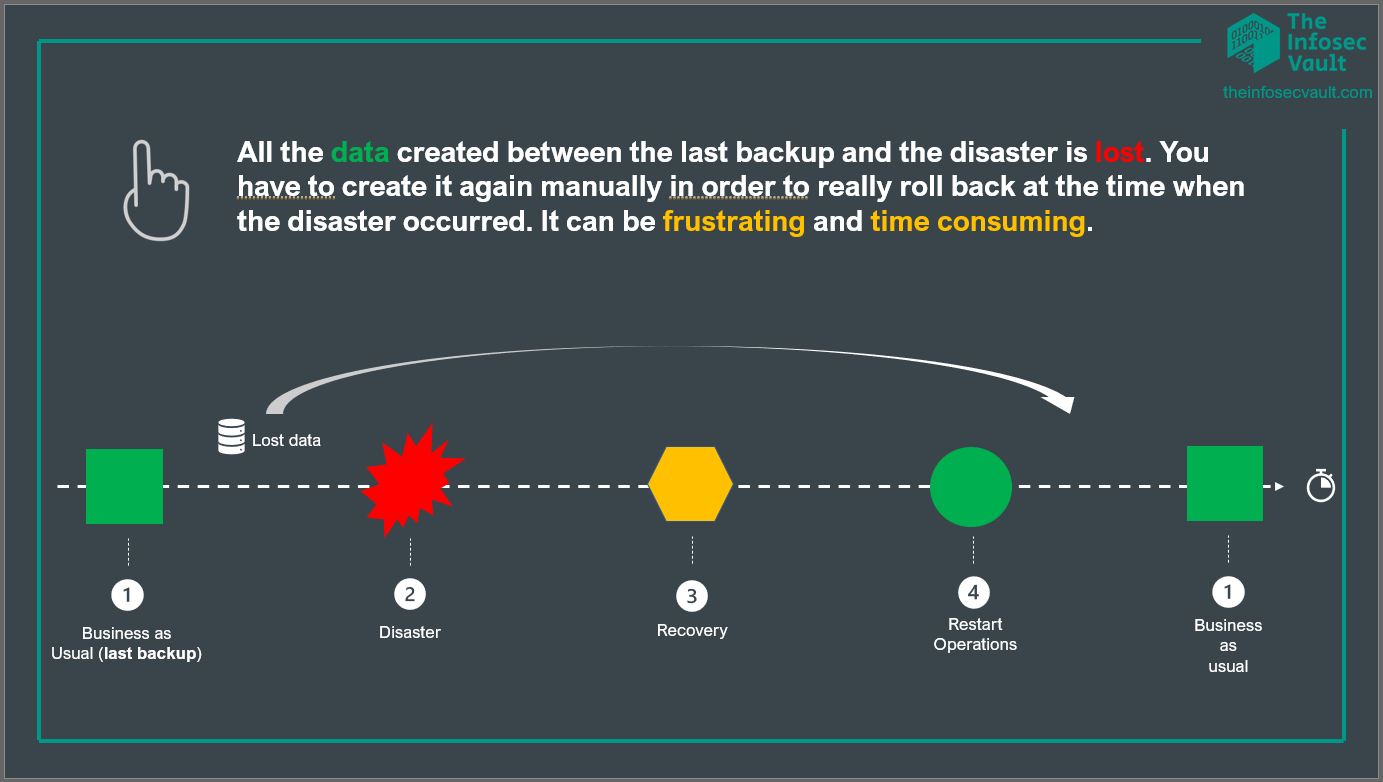
• All the data created between the last backup and the disaster is lost. You have to create it again manually in order to really roll back at the time when the disaster occurred. It can be frustrating and time consuming.
• Data lost is a waste of time, a damage for your stakeholders and probably a violation of the privacy law (if you are a Data Controller of a SME we provided a recap of your duties here: https://www.theinfosecvault.com/2023/09/14/demystifying-gdpr-your-essential-guide-for-smes-and-consultants/)